On Tuesday, July 29th, DigiCert’s UltraDDoS Protect service successfully mitigated an internet tsunami, a massive DDoS attack that reached 2.4 Terabits per second (Tbps) of bandwidth and 553 Million packets per second (Mpps) of impact. This is the largest attack that has been recorded to date on the UltraDDoS Protect Network.
Tbps+ DDoS attacks – internet tsunamis
Tsunamis have been in the news lately because of the 8.8-Magnitude earthquake that struck just off the coast of Russia that sent waves cascading throughout the Pacific Ocean. The tsunami impacted Japan and locations as far off as Hawaii and the US west coast, triggering alerts and actions across many coastal nations to prepare for the worst-case scenario. The actual waves caused by this event were more moderate than originally feared and appropriate protections were in place, so the damage caused was thankfully minimal. Despite it not being as severe as was predicted, the event has made coastal cities re-evaluate their defenses against tsunamis so that they are even more prepared for the next one.
Internet tsunamis are Tbps or larger DDoS attacks that mirror many of the characteristics of ocean tsunamis. An internet tsunami can come at any time with little to no warning, impact any business that connects to the internet, may be followed by continued attacks after the initial burst, and do damage that may take a prolonged time to fix if the right protections aren’t in place. The one major difference between the two is that ocean tsunamis take time to make it across oceans before striking. This can provide time to brace for the impact. Internet tsunamis, on the other hand, generally ramp up immediately giving victims no time to react. To learn more about the botnets and tactics behind these large attacks, I recommend this blog by my colleague Bryant Rump covering the Aisuru botnet and an internet tsunami that it was used for.
Companies have a finite amount of bandwidth over which they connect to the internet, and many have protections from DDoS that can handle some DDoS attacks. Coastal regions and cities have protections against storm surges and extremely high tides, but most cannot handle a tsunami on their own. Similarly, extremely few businesses are equipped to handle a Tbps+ attack on their own without partnering with a provider that can.
Examining the multi-Tbps DDoS attack from July 29, 2025
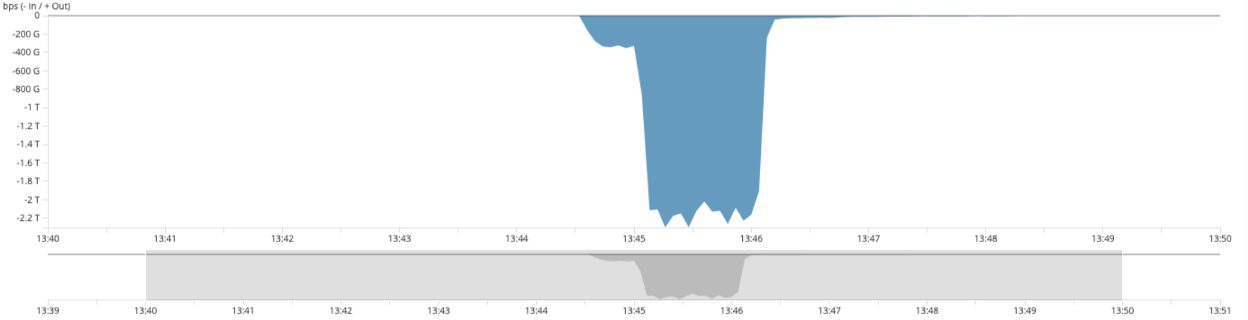
The 2.4 Tbps internet tsunami DDoS attack that hit the UltraDDoS Protect network was directed towards an always-on customer based in the EMEA region. It was a carpet bomb DDoS attack where traffic was directed to many destination IP addresses within the customer network. Nearly 800 unique IPv4 addresses were targeted. This means that the attacker was indiscriminate as to what was affected within the victim’s IP address space. Multi-Tbps DDoS attacks tend to be indiscriminate in nature anyways because they often cause collateral damage well beyond the intended target.
The main characteristics of this attack included:
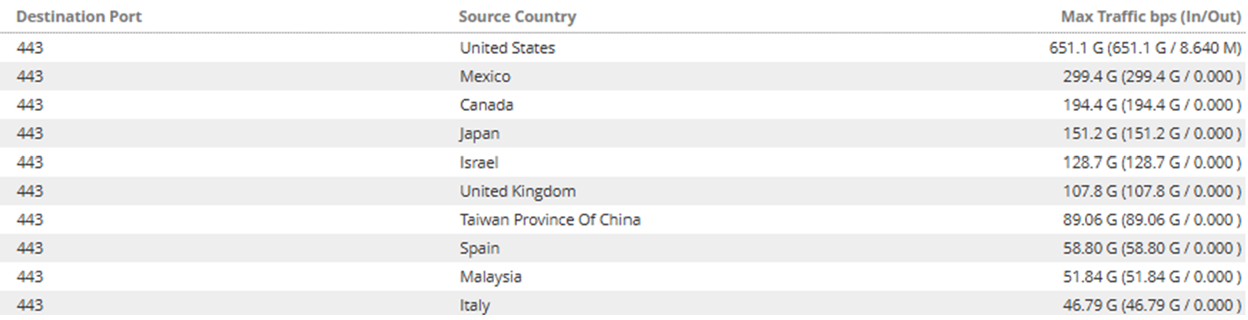
- The attack sources were widely distributed with the United States, Mexico, Canada, Japan, Israel and Taiwan being the highest contributing countries.
- All traffic was destined to port 443 which is the default for most web traffic so it could not be simply filtered at the network border.
- Extremely short time duration (< 1 minute) for the attack peak of 2.387Tbps/552.6Mpps.
- Approximately 3Gbps per destination IP (~800 target IP addresses).
- Multiple smaller follow-on attacks after the initial surge.
Mitigating an internet tsunami
Mitigating an attack of this magnitude is done in stages. The first stage is to withstand the initial surge in traffic to keep it from getting to the customer’s resources. These are your time 0 defenses and require that the customer be always routing their traffic through the DDoS protection network. An effective DDoS protection network requires a lot of available bandwidth – we have over 15 Tbps – strong networking controls and filtering capabilities at all borders of the network. The DDoS service must be able to absorb the sudden influx in traffic and shunt most of it away from the customer until more aggressive countermeasures can be applied. The second stage can take effect shortly after the attack starts – our SLA is under 30 seconds – where automation applies more aggressive DDoS countermeasures to the customer’s traffic to discern attack traffic from legitimate traffic. The third stage is to have an experienced analyst review what is being passed and dropped, communicate and collaborate with the customer to ensure the mitigation is completely effective, and if not, make the necessary adjustments.
The multi-Tbps surge that occurred with this attack lasted less than 1 minute before dropping down to much smaller bandwidth levels so the actual tsunami DDoS attack only passed through the first stage of protection. We withstood the traffic on behalf of the customer, so they had extremely minimal initial impact and no lasting impact from the gigantic attack. This was possible because they were deployed always-on through the UltraDDoS Protect network. If they had been deployed for on-demand protection, the initial tsunami wave would have hit the customer directly at first and even after diverting traffic to our DDoS service, the impact would have already been made. This is one of the reasons that always-on is the best practice for DDoS Protection.
Continuous Improvement in DDoS Defense
Coincidentally, we effectively mitigated a much longer lasting carpet bomb attack that topped out over 700 Gbps along with many other smaller mitigations on the same day. The architecture and capacity of our network and the expertise of our team is what makes this possible to effectively handle days like this. It’s what we do.
We are not sitting back on our laurels to celebrate another successful day mitigating DDoS attacks for our customers, however. We believe in continuous improvement in the services we provide so every situation, especially more extreme cases like this one, provides us opportunities to improve. The SOC, network engineering, engineering and product teams meet regularly to go through what went well and what things we could improve upon, and we make the necessary changes to our architecture, process and customer service. When the next internet tsunami targets one of our customers, we’ll be even more prepared.
For more information about the DigiCert UltraDDoS Protect Solution and how we can protect your organization from large-scale attacks, please visit our solution page.
