Business operations rely on the organization’s digital infrastructure, with everything from internal applications to customer-facing websites relying on continued availability. Recognizing the importance of connectivity, cybercriminals increasingly target the digital infrastructure, seeking to disrupt operations.
For security teams, threat intelligence provides some insight into the types of attacks deployed in the wild. However, many still face challenges in gaining insight into hard-to-track attack types, like Distributed Denial of Service (DDoS) attacks, where threat actors deploy evasion techniques with carpet bombing attacks. To protect business reputation and customer trust, organizations need to monitor for and protect against damaging service disruptions.
This monthly roundup of reports provides information to help defenders manage their cloud-based security.
Every month, Vercara reports on trends across three critical infrastructure domains:
- Distributed Denial of Service (DDoS) attacks
- Domain Name Service (DNS) traffic
- Web Application Firewall (WAF) attacks
DDoS: Law enforcement operations impact attackers
Overall, DDoS attacks saw a 36.17% month-over-month decrease, which is likely tied to law enforcement’s Operation PowerOff at the beginning of December to disrupt malicious actors’ ability to conduct DDoS attacks during the holiday season. Of the data gathered, the following highlights offer insights:
- 3,102 DDoS attacks detected, with Vercara’s monitoring and mitigation preventing approximately 1,137 hours of downtime
- 75% increase in mega attacks when compared to November
- 762.16% increase in attacks generating 500,000 to 1 million packets per second, indicating threat actors making tactical shifts to prioritize packet volume over bandwidth.
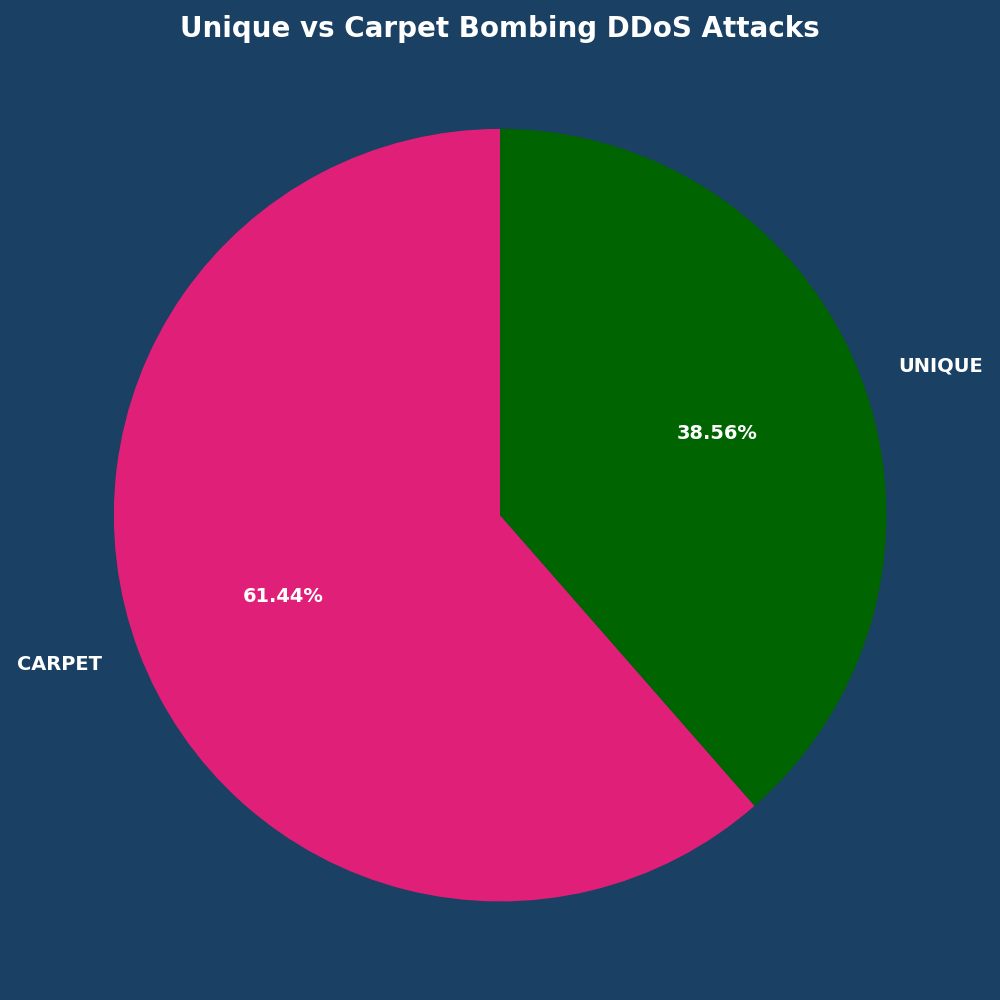
- Carpet bombing attacks accounted for 61% of all observed DDoS attacks in December 2024
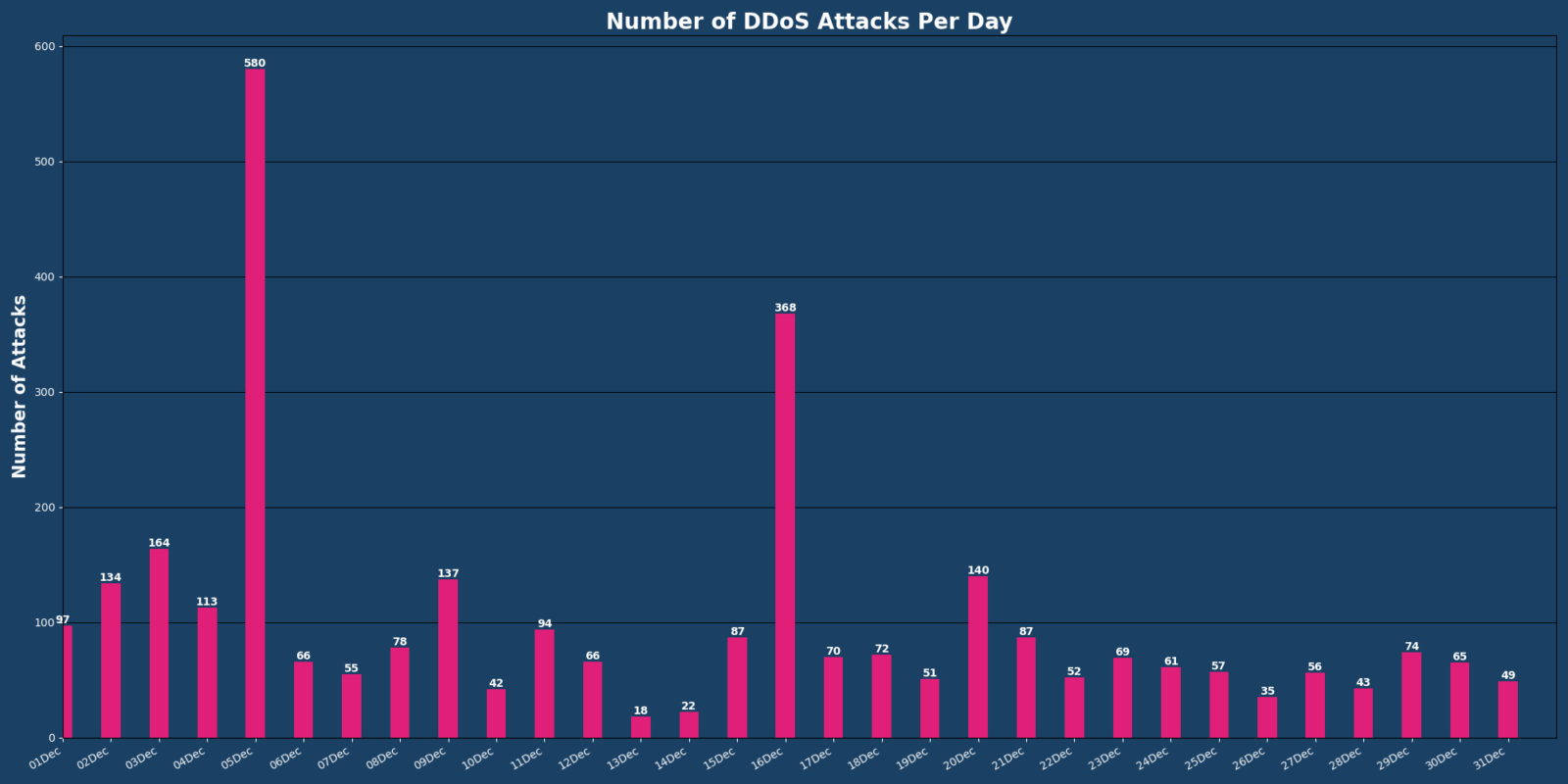
For more details, see the DDoS Analysis report.
Carpet bombing continues to prevail
In carpet bombing DDoS attacks, malicious actors target numerous IP addresses with smaller-sized attacks to evade detection, making mitigation more difficult. Small attacks between 0-0.5 GBPS accounted for 70.98% of December DDoS attacks.
Carpet bombing attacks remain the primary threat, but the largest increase in gigabit per second attacks were attacks consisting of 10-50 Gbps which saw a 117.89% increase suggesting that malicious actors potentially shifted their Tactics, Techniques and Procedures (TTPs) to focus on larger packet attacks to degrade network performance more effectively. This shift in TTPs aligns with the observed trends in malicious actor behavior, where targeting high packet rates can overwhelm network infrastructure even when overall attack bandwidth decreases.
Comparing month-to-month changes notes the following:
- Small attacks (0-0.5 gbps): -40.35%
- Mega Attacks (100+ Gbps): 75%
While mega attacks (100+ Gbps) saw 75% increase in December compared to November, they only accounted for 7 of all DDoS attacks (approximately 0.23% of all DDoS attacks).

Since most organizations typically set alert triggers at higher gigabit levels, carpet bombing DDoS attacks create mitigation challenges because the threat actors:
- Remain under alerting thresholds
- Flood networks
- Rotate target IPs and destinations
- Rotate targeting method
Top 3 attack vectors remain mostly static
Total Traffic as an attack vector maintained its number one spot. While some shifts across the top four occurred in terms of percentages, the top three remained the same compared to November.
The top four attack vectors for December were:
- Total Traffic: 30.78% (compared to November’s 47.76%)
- TCP ACK: 14.43% (compared to November’s 11.44%)
- UDP: 14.07% (compared to November’s 16.86%)
- TCP SYN/ACK Amplification: 10.91%
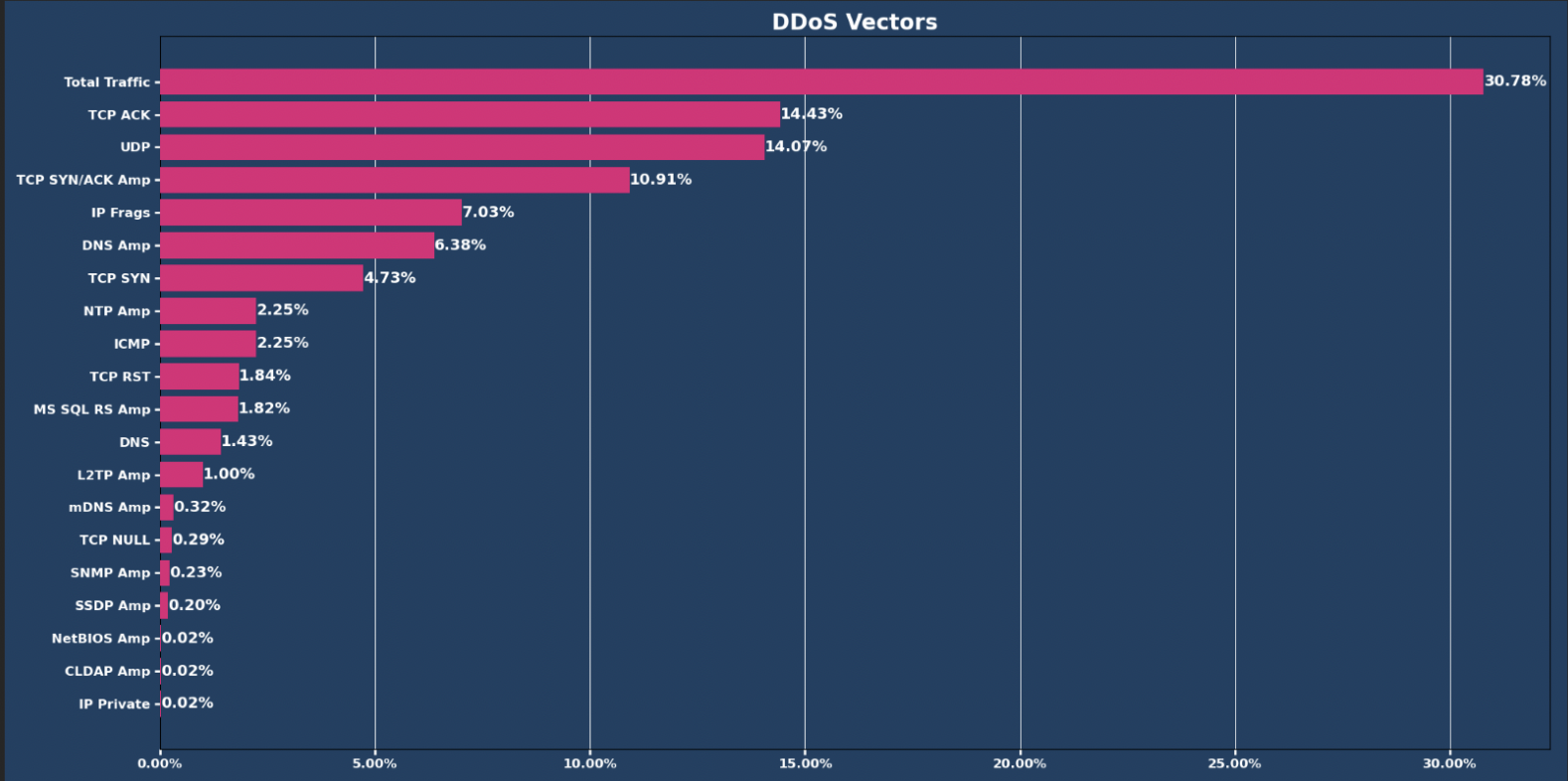
The number of observed DDoS attacks consisting of one DDoS vector decreased from 78.81% in November to 48.65% in December.
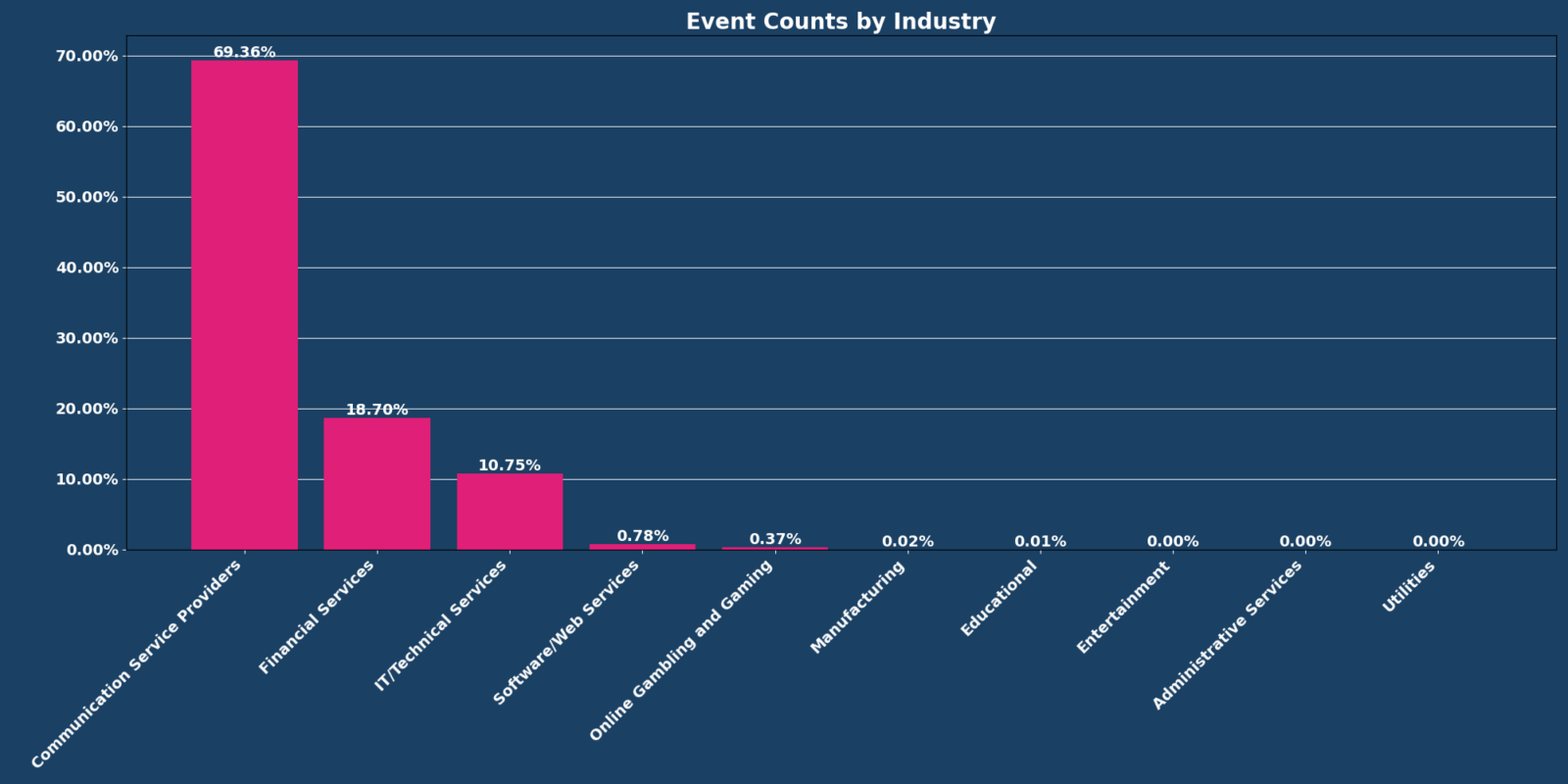
Top 3 industries
December’s top three industries by percentage of events were:
- Communication service providers: 69.36% (compared to November’s 28.16%)
- Financial Services: 18.78% (compared to November’s 60.27%)
- IT/Technical Services: 10.75%
DNS: Small shifts offer larger insights
As a longer month compared to November, Vercara Managed DNS noted a 1.49% increase in overall web traffic for December while marking a significant milestone of over 4.2 trillion DNS queries processed through the DNS servers.
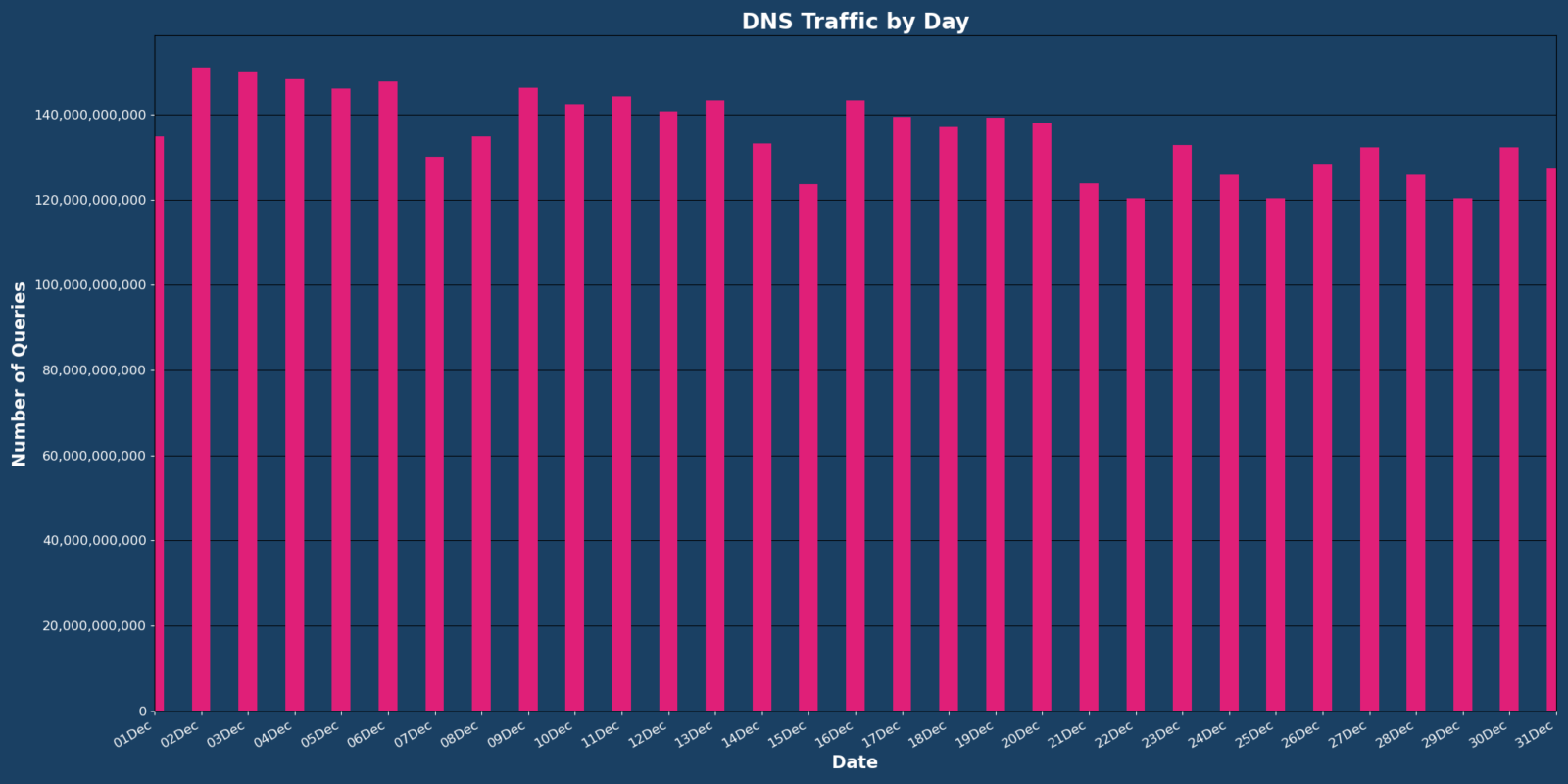
Vercara’s UltraDNS observed 157 DDoS attacks targeted against the platform in December, a 190.74% increase compared to November’s 101.
To learn more, see the DNS Analysis report.
IPv4 and IPv6 trends
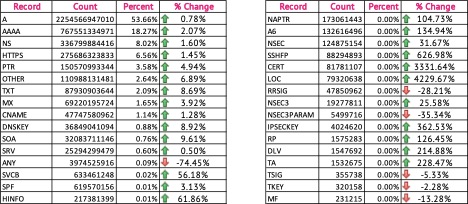
Overall, December followed in November’s footsteps with the Top 3 DNS Query types:
- A Record
- AAAA record (quad-A)
- Name Server (NS)
The consistent percentage of quad-A record queries indicates a continued shift toward IPv6 and its additional security benefits.
Notably, the Location (LOC) DNS record type, used to store geographic location data associated with a domain or host, saw a 4,220.67% increase compared to November.
DNS response codes remain statistically stable
The top two response codes remained the same month-over-month:
- “No Error”: most prevalent response code at 78.25%, a 3.56% month-over-month increase
- “NXDomain”: 21.33%, a 4.84% month-over-month decrease
The NX Domain response code can indicate a misconfiguration or attackers using DNS enumeration tools that can cause a DDoS attack.
Industry sectors
Industry sectors continue to work on and improve their DNS management, with December’s report showing both wins and areas for improvement.
Generally, the DNS record-type queries provide insight into how the industry uses digital infrastructure. Some highlights include:
- Widespread requests for HTTPS records indicate an emphasis on secure web communications.
- Gaming and Gambling focus on MS records indicates the importance of reliable email communications.
Software/Web Services and IT/Technical Services
These two industries received the most DNS queries, representing 80.05% of all DNS queries. Software/Web Services accounted for 46.01%, while IT/Technical Services accounted for 34.04%. The number indicates the sectors’ extensive reliance on robust DNS services for:
- Web hosting
- Cloud services
- Technical operations
Additionally, the Software/Web Services industry had a significant presence of ‘No Error’ responses, indicating effective DNS management.
Financial Services and Health Care
These two industries show a moderate presence of TXT records that indicate heightened emphasis on email authentication protocols like SPF or DKIM, signaling stronger cybersecurity awareness in sectors
Web Application Firewall (WAF): Increased malicious and bot traffic
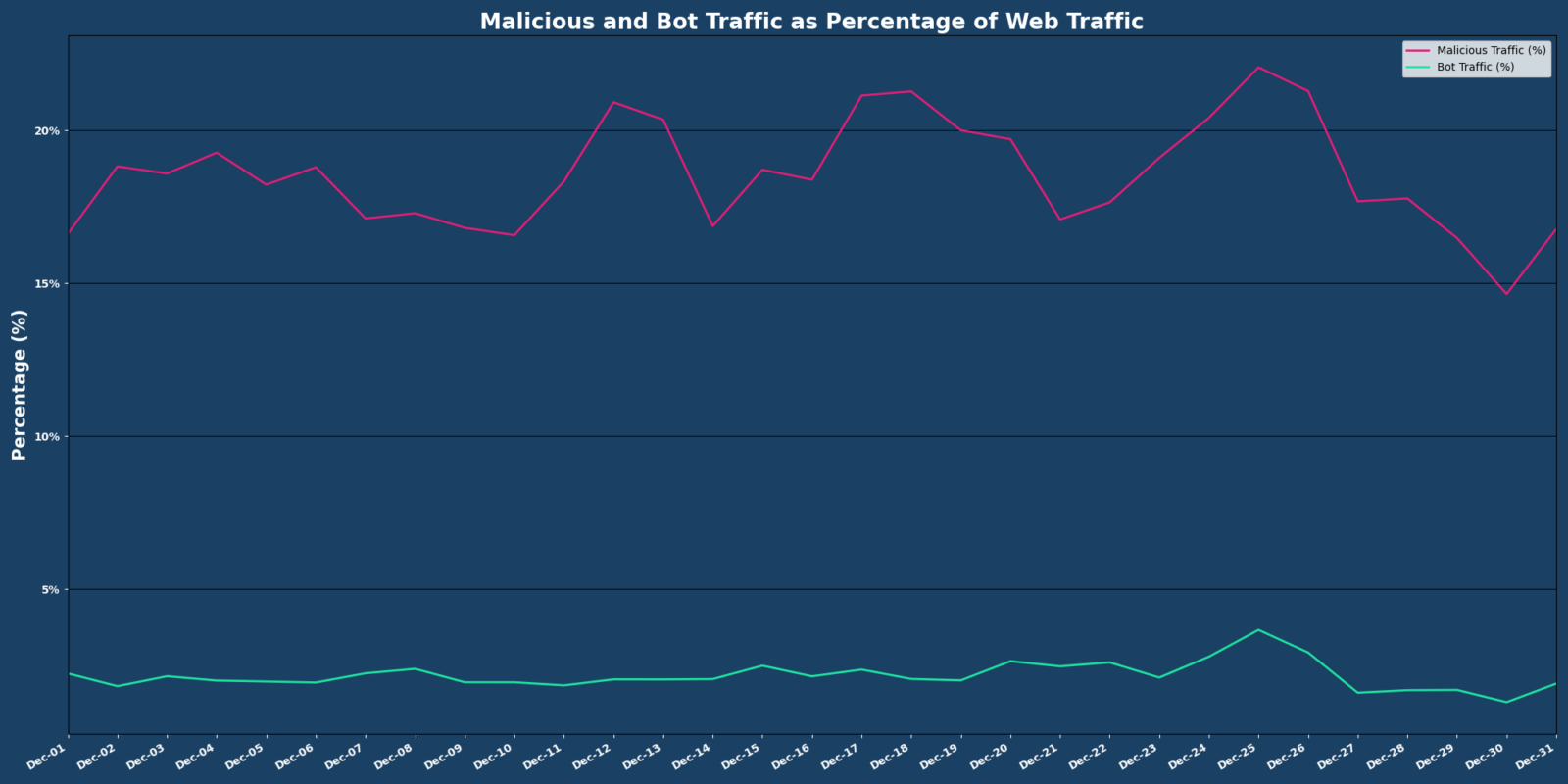
During December, Vercara UltraWAF processed over 580 million web requests, a 1.72% decrease compared to November. Of these requests, 18.47% were malicious and 2.11% were identified as bot traffic.
Notable payloads targeted vulnerabilities in frameworks like Sympfony, Jenkins, and Spring Boot. These payloads aimed to:
- Exfiltrate sensitive files
- Execute arbitrary code
- Exploit database errors
To learn more, see the WAF Analysis report.
Get down…with malicious and bot activity
December’s data found:
- 3.56% decrease in malicious activity compared to November
- 25.30% decrease in the amount of bot traffic compared to November
Top 3: the more things change, the more they stay the same
Along with these overall increases, December showed additional changes:
- Cookie threat category remained most prevalent, accounting for 41.56% of malicious traffic
- Command Injection came in second, accounting for 26.53% of malicious traffic
- Invalid RFC threat came in third, accounting for 14.15% of malicious traffic

December countermeasure of the month
Our featured countermeasure this month is Bot Trap, which detects scraping bots by adding unique links to an HTML page that only bots and other automated programs can follow. The system can effectively identify and block bots without impacting the user experience.
Vercara recommends adding Bot Trap to a variety of pages that host or receive HTML forms, such as:
- Website search
- Shopping carts
- Login, logoff, and password reset
- Dynamically-generated pages backed by a database
- Contact us, talk to sales or any other incoming inquiries
Turnkey Cloud-based Security with Vercara
Vercara provides a turnkey, multilayered approach to security with UltraDNS, UltraDDoS, and UltraWAF. With Vercara’s comprehensive suite of solutions, organizations gain advanced security capabilities, insights for informed decision-making, and improved resilience against cyber threats.
To learn how Vercara’s suite of solutions can help defend your organization, contact our sales team.
