Any disruption to a company’s digital infrastructure creates business interruptions that undermine an organization’s revenue and profitability goals. Organizations rely on infrastructure such as their data centers, network connectivity, and the Domain Name System (DNS) as the foundation for their digital business operations, including internal applications and customer-facing websites and services.
As attackers continue to target these operations and the infrastructure that supports them, security teams work tirelessly to mitigate risk and protect sensitive data and assets. For insights into Distributed Denial of Service (DDoS) attacks, security teams need current threat intelligence from experts who understand the Tactics, Techniques, and Procedures (TTPs) that threat actors use to evade detection and mitigation, such as carpet-bombing attacks.
Every month, Vercara reports on trends across three critical infrastructure domains:
- Distributed Denial of Service (DDoS) attacks
- Domain Name Service (DNS) traffic
- Web Application Firewall (WAF) attacks
This monthly roundup of reports provides information to help defenders manage their infrastructure, applications, and cloud-based security solutions.
DDoS: Attackers Shifting Tactics After Law Enforcement Operations
Overall, DDoS attacks saw a 60.61% month-over-month increase, likely related to the growing sophistication and accessibility of DDoS-for-hire services, exploitation of vulnerable Internet-of-Thing (IoT) devices, and shifting attack methodologies.
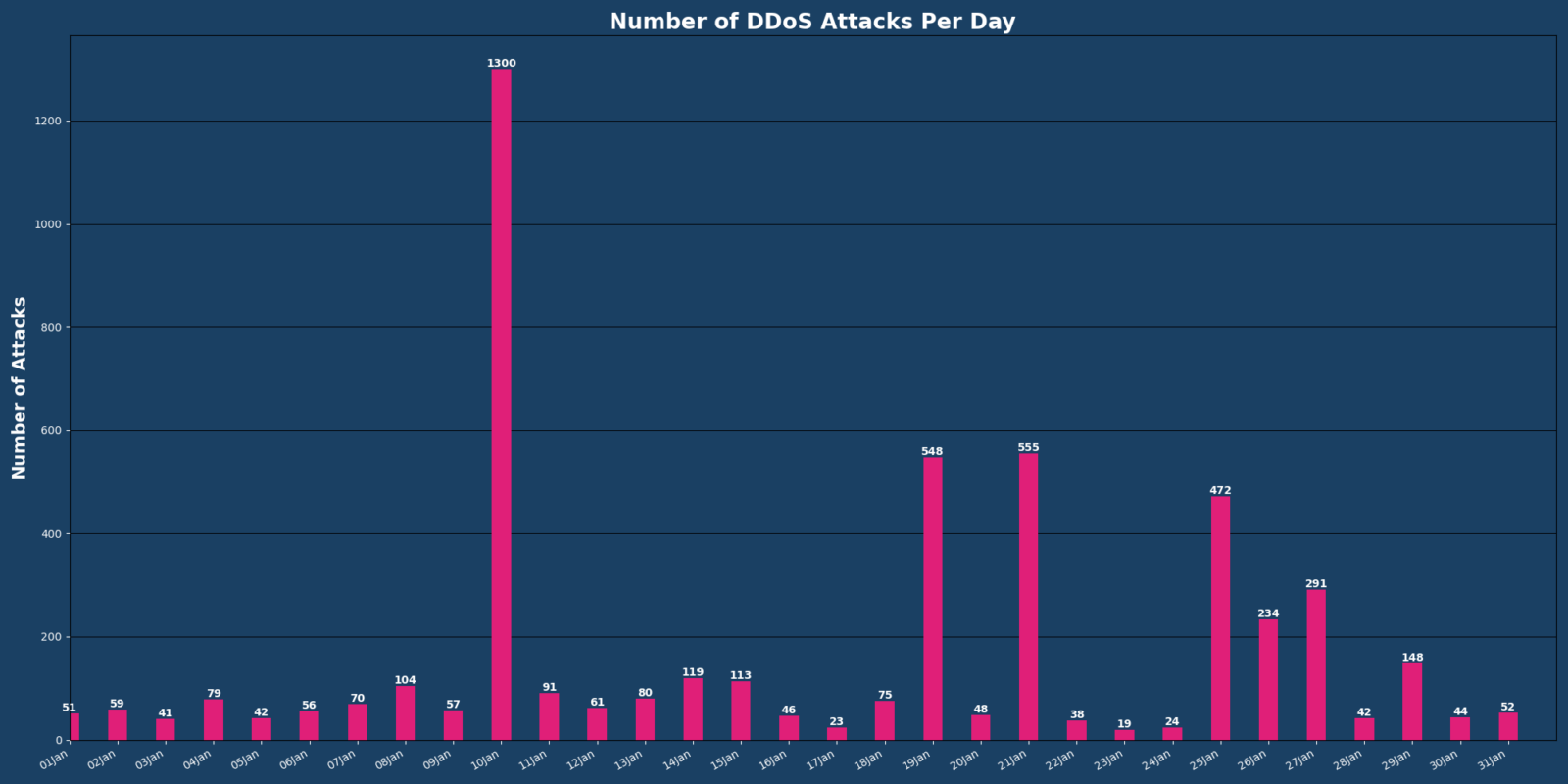
Of the data gathered, the following highlights offer insights:
- 4,982 DDoS attacks detected, with Vercara’s monitoring and mitigation preventing approximately 2,485 hours of downtime
- 71% decrease in mega attacks when compared to December, likely due to law enforcement takedown operations against major botnet infrastructures
- 72% of observed attacks measured under 0.5 Gbps, reflecting a strategic shift by attackers toward low-bandwidth, high-frequency attack
For more details, see the DDoS Analysis Report.
Carpet Bombing is Back Again
When malicious actors target numerous IP addresses with smaller-sized attacks, called carpet bombing, they intend to evade detection and make mitigation more difficult. Small attacks between 0-0.5 GBPS accounted for 3,610 of the 4,982 DDoS attacks in January, getting back to normal after the December slump. Mega attacks only accounted for two of all DDoS attacks, approximately 0.04%.
Carpet bombing attacks account for 79.97% of the January DDoS attacks observed.
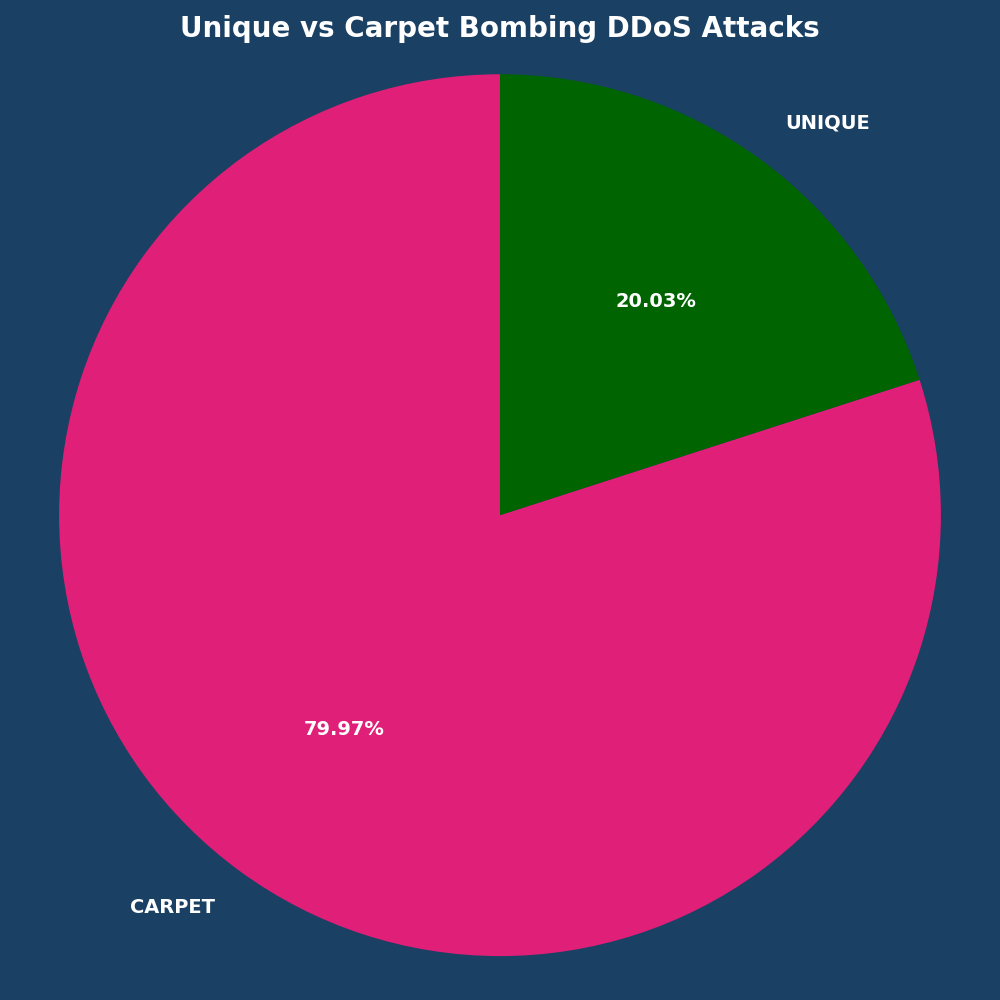
Comparing month-to-month changes notes the following:
- Small attacks (0-0.5 Gbps): 64.02%
- Mega Attacks (100+ Gbps): -71%
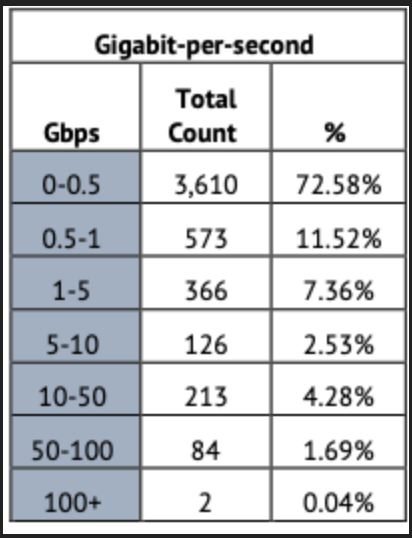
Since most organizations typically set alert triggers at higher gigabit levels, carpet bombing DDoS attacks create mitigation challenges because the threat actors:
- Remain under alerting thresholds
- Flood networks
- Rotate target IPs and destinations
- Rotate targeting method
Top 3 Attack Vectors Shift a Bit
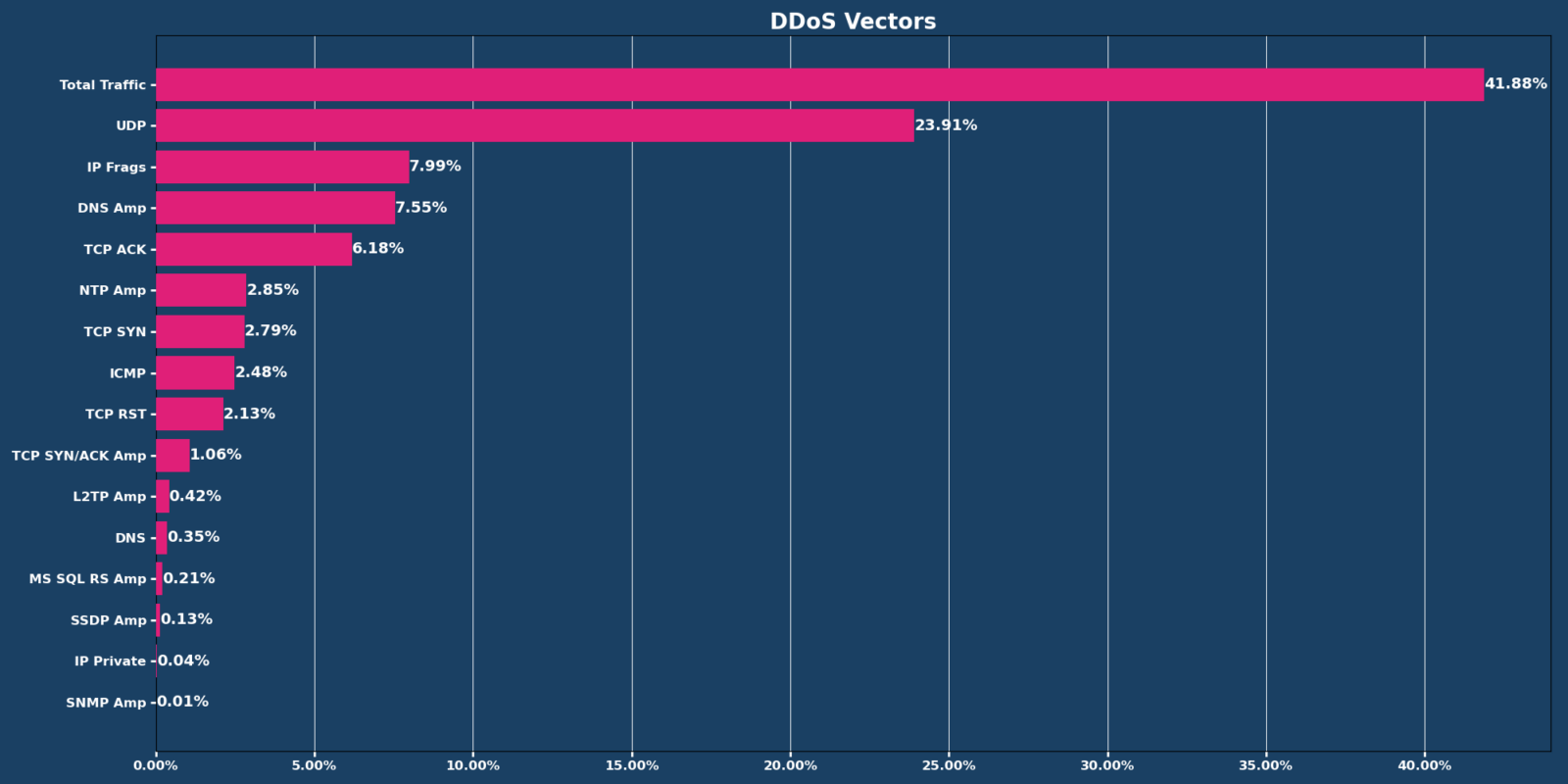
Total Traffic as an attack vector maintained its number one spot. Compared to December, the top four attack types saw a few additions.
The top four attack vectors for January were:
- Total Traffic: 41.88% (compared to December’s 30.78%)
- UDP: 23.91% (compared to December’s 14.07%)
- IP Frags: 7.99%
- DNS Amp: 7.55%
58.59% of observed DDoS attacks consisted of one DDoS vector while 41.41% consisted of two or more.
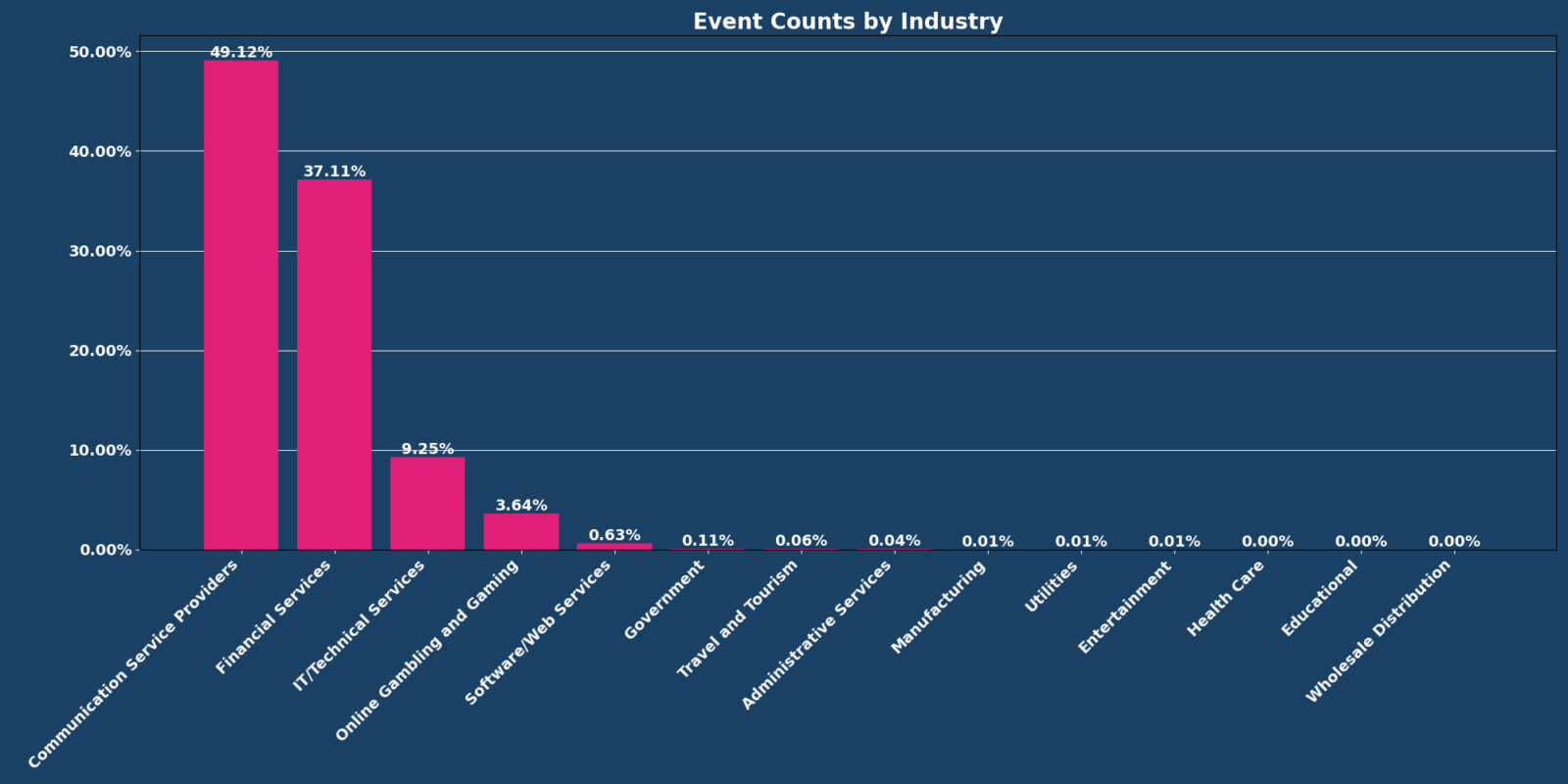
Top 3 Industries
The top 3 most targeted industries remained static, with January’s top three industries by percentage of events listed as:
- Communication service providers: 49.12% (compared to December’s 69.36%)
- Financial Services: 37.11% (compared to December’s 18.78%)
- IT/Technical Services: 19.25 (compared to December’s 0.75%)
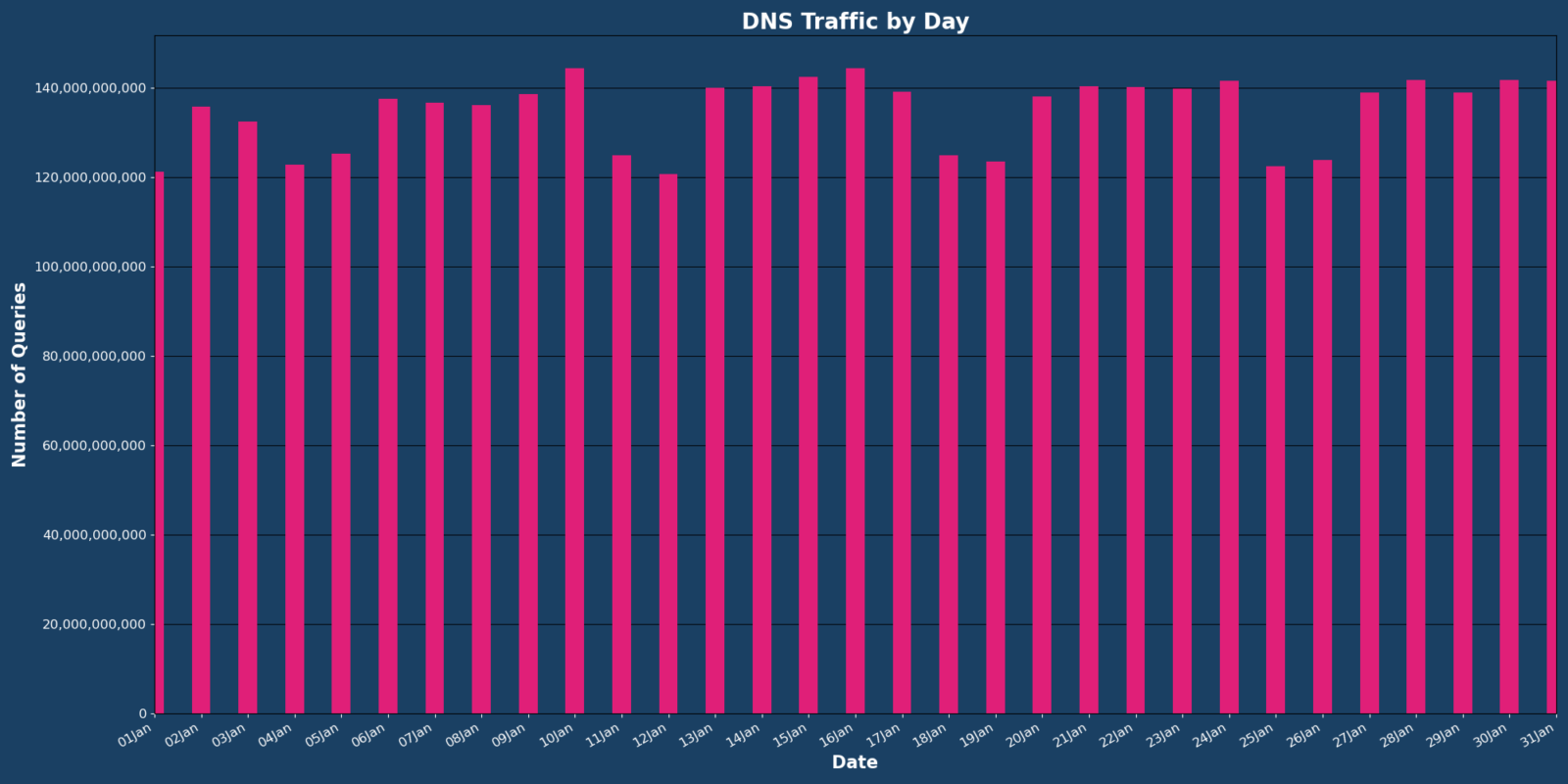
DNS: No News is Good News
Vercara Managed DNS noted a .44% decrease in overall web traffic for January, with the average number of authoritative queries per day being approximately 134.93 billion queries, highlighting how important digital infrastructure has become.
Vercara’s UltraDNS observed 63 DDoS attacks targeted against the platform in January, a marked decrease compared to December’s 157.
For more details, see the DNS Analysis Report.
IPv4 and IPv6 trends
Overall, January followed in December’s footsteps with the Top 3 DNS Query types:
- A Record
- AAAA record (quad-A)
- Name Server (NS)
The consistent percentage of quad-A record queries indicates a continued shift toward IPv6 and its additional security benefits.
Notably, the Trust Anchor (TA) DNS record type, used in DNSSEC to help ensure secure DNS resolution by allowing resolvers to authenticate DNSSEC-signed domains independently, saw a 127.18% increase compared to December.
DNS Response Codes Remain Statistically Stable
The top two response codes remained the same month-over-month:
- “No Error”: most prevalent response code at 78.25%, a 3.56% month-over-month increase
- “NXDomain”: 21.33%, a 4.84% month-over-month increase

The NX Domain response code can indicate a misconfiguration or attackers using DNS enumeration tools that can cause a DDoS attack.
Industry Sectors
Industry sectors continue to work on and improve their DNS management, with January’s report showing both wins and areas for improvement.
The DNS record-type queries provide insight into how the industry uses digital infrastructure. Some highlights include:
- Widespread requests for HTTPS records indicate an emphasis on secure web communications.
- Financial Services and Healthcare verticals show a moderate presence of TXT records, indicating a heightened emphasis on email authentication protocols like SPF or DKIM.

Software/Web Services and IT/Technical Services
These two industries received the most DNS queries, representing 77.84% of all DNS queries. Software/Web Services accounted for 46.09%, while IT/Technical Services accounted for 31.75%. The number indicates the sectors’ extensive reliance on robust DNS services for:
- Web hosting
- Cloud services
- Technical operations
Additionally, the Software/Web Services industry had a significant presence of ‘No Error’ responses, indicating effective DNS management.
Agriculture/Food Production and Wholesale Distribution
These two industries show a lower adoption of advanced DNS features, aligning with the diverse ways the verticals use connected technologies.
Web Application Firewall (WAF): Up, Up…But Not Away
During January, Vercara UltraWAF processed over 713 million web requests, a marked 22.96% decrease compared to December. Of these requests, 16.29% were malicious, and 1.73% were identified as bot traffic.

Notable payloads targeted vulnerabilities in frameworks like Sympfony, Jenkins, and Spring Boot. These payloads aimed to:
- Exfiltrate sensitive files
- Execute arbitrary code
- Exploit database errors
For more details, see the WAF Analysis Report.
Holding Statistically Steady
January’s data found:
- 8.42% increase in malicious activity compared to December
- 1.23% increase in the amount of bot traffic compared to December
Top 3: the More Things Change, the More They Stay the Same
Along with these overall increases, January showed additional changes:
- Cookie threat category remained most prevalent, accounting for 43.39% of malicious traffic
- Command Injection came in second, accounting for 22.05% of malicious traffic
- Invalid RFC threat came in third, accounting for 17.26% of malicious traffic

January Countermeasure of the Month
Our featured countermeasure this month is Block Countries configuration that a WAF administrator can use to block entire countries based on Geo-IP data. For example, financial services organizations can use the list to block countries on the Office of Foreign Asset Control (OFAC) list as part of their Bank Secrecy Act (BSA) compliance objectives. Additionally, admins can add countries to the list for a brief period of time if threat intelligence indicates application-layer DDoS attacks being deployed from the location.
Turnkey Cloud-based Security with Vercara
Vercara provides a turnkey, multilayered approach to security with UltraDNS, UltraDDoS Protect, and UltraWAF. With Vercara’s comprehensive suite of solutions, organizations gain advanced security capabilities, insights for informed decision-making, and improved resilience against cyber threats.
Contact our sales team to learn how Vercara’s suite of solutions can help defend your organization.
