While breaking records might be good in sports, it’s not always the best for security. Organizations rely on their digital infrastructure to ensure continued business operations. To maintain business continuity, companies need insights into the threats facing their infrastructures to implement appropriate mitigation strategies.
Every month, Vercara reports on trends across three critical infrastructure domains:
- Distributed Denial of Service (DDoS) attacks
- Domain Name Service (DNS) traffic
- Web Application Firewall (WAF) attacks
DDoS: Business Interruption – Slow and Steady or Fast and Targeted?
While setting an all-time high record in scoring goals is an achievement, setting a record like that for DDoS attacks is a concern.
June brought with it two notable records:
- 55,630 DDoS attacks, setting an all-time Vercara record for 2024 with a 288% month-over-month increase compared to May 2024
- 420 million packets per section (pps) attack, a 20% increase from the previous record
See the latest DDoS Analysis report for more details.
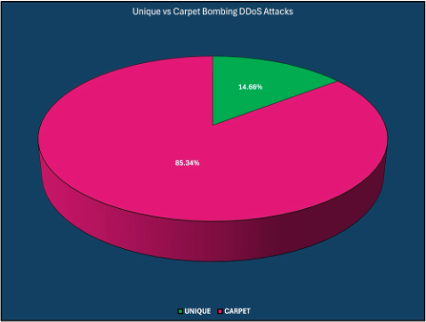
Continued Upward Trend for Carpet Bombing DDoS Attacks
Fueled by regional conflicts, hacktivists continue to focus on disrupting organizations, industries, and countries with carpet bombing DDoS attacks that spread smaller attacks over an entire target network block. Attackers use this strategy to evade detection and make mitigation more difficult by changing targeted destinations and DDoS vectors. While mega attacks saw a significant month-over-month increase in June, they remained a small percentage of overall attacks.
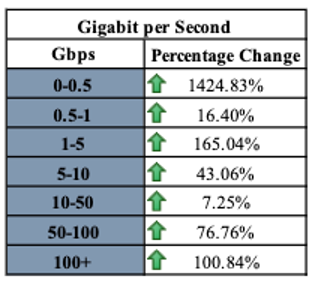
The continued rise of carpet bombing attacks, evidenced by smaller gigabit per second (Gbps) floods, likely indicates less sophisticated attackers using DDoS-for-hire or botnet services to achieve their objectives. However, the few mega attacks remain notable since they likely indicate more sophisticated threat actors.
- Small attacks (0-0.5 Gbps): 1424.83% increase from the previous month
- Mega Attacks (100+ Gbps):100.84% increase but only 0.43% of all observed attacks
For most organizations, carpet bombing DDoS attacks create mitigation challenges since organizations often set alert triggers at higher gigabit levels. However, in a carpet bombing DDoS attack, the threat actors:
- Remain under alerting thresholds
- Flood networks
- Rotate target IPs and destinations
- Rotate targeting method
Resurgence of DNS Amplification
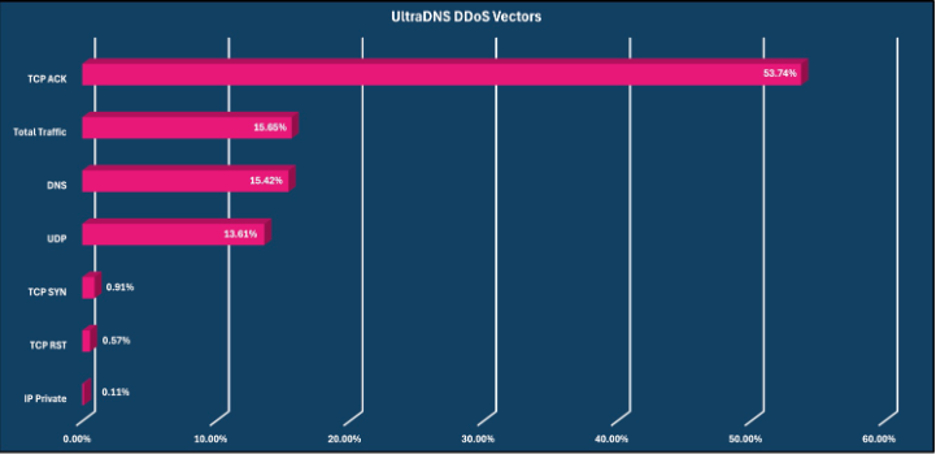
On the rise through 2023, DNS Amplification attacks became the top DDoS attack vector for the first time in 2024. The top three attack vectors for June were:
- DNS Amplification: 38.94%
- IP Fragmentation: 21.04%
- Total Traffic: 15.37%
Of note, 66.11% of observed DDoS attacks for June consisted of a single attack vector.
Top 3 Industries
The top three industries for June 2024 shifted a bit compared to May:
- Financial Services: increased by 46.01% from May
- Communication service providers: decreased by 18%
- Software/Web Services: increased by 141%
Most month-over-month position changes relate to month-over-month increases for financial services and software/web services rather than an overarching decreasing number of attacks against other industries.
DNS: Purposeful Security Shifts
June was a shorter month than May, and Vercara Managed DNS noted a 4.12% decrease in overall web traffic for June, making comparisons between the months a bit more difficult.
From a protection standpoint, Vercara’s UltraDNS mitigated 528 DDoS attacks targeted against the platform, exhibiting a 236.31% month-over-month increase. The most significant DDoS attack exceeding mitigation thresholds and observed against UltraDNS was 0.51 Gbps, lasting approximately 30 minutes. Notably, these attacks do not include smaller ones that the platform automatically mitigated.
Slow and Steady IPv6 Trends
Overall, June followed in May’s footsteps with the 3op 3 DNS query types:
- A Record
- AAAA record (quad-A)
- Name Server (NS)
The quad-A record queries indicate a continued shift toward IPv6 and its additional security benefits. While A Record and NS Record queries decreased in alignment with the overall decreased queries, the quad-A record queries remained nearly the same, accounting for 18.09% in June compared to 18.25% in May.
As this shift continues at a constant pace, organizations should keep records current and update configurations.
DNS Response Codes: Configuration or Enumeration?
The top two response codes remained the same month-over-month:
- “No Error”: most prevalent response code at 77.11%
- “NXDomain”: 22.19%
The NX Domain response code can indicate a misconfiguration or attackers using DNS enumeration tools that can cause a DDoS attack.
Industry Sectors Focus their Security Efforts
Industry sectors increasingly align their security efforts with activities related to their business objectives.
Management and Education
In June, these two industry sectors focused on HTTPS resource records. From a security perspective, this activity shows movement toward low-cost but high-impact security improvements, especially for the Education sector, which often faces budget constraints.
IT/Technical Services and Software/Web Services
These sectors focused activities on TXT and CNAME configurations. As technical industries that rely on their cloud-based infrastructure, this approach aligns with their ability to implement more advanced configurations and security measures.
Gaming and Gambling
This sector prioritized ‘MX’ records, which aligns with the need for reliable email communications. Since these organizations primarily communicate with customers via email, this focus helps them reduce the likelihood that email providers will flag them as spam.
Web Application Firewall (WAF): Bots, Bots, and More Bots
Despite the overall decrease in web traffic for June, Vercara UltraWAF detected a steady month-over-month bot traffic increase.
The Rise of Bots
Malicious activity accounted for 15.68%, representing an 80.13% month-over-month decrease. Despite the reduced malicious activity, bot traffic showed a 2.12% month-over-month increase, accounting for 1.82% of all web traffic.
Washing the Digital Hands
Cyber hygiene remains critical. The 400 Response category experienced an 86.38% increase. Since this is related to client-side issues, the data indicates that organizations need to stay vigilant about API hygiene to mitigate risks and implement countermeasures like:
- Detecting large URLS to mitigate Buffer Overflow Risks
- Implementing input validation and sanitation to mitigate SQL injection and command injection attacks.
- Limiting request sizes to mitigate SQL injection and command injection attacks.
June Countermeasure of the Month
Over the last month, Vercara WAF discovered high volumes of requests to “/AutoDiscover/autodiscover.xml” coming from Microsoft Office. Although this can arise from a Microsoft Outlook autodiscovery process, attackers can use this to discover additional hosts to attack.
Inside the Deny URL countermeasure, WAF administrators can block specific URIs with a regular expression.
Turnkey Cloud-Based Security with Vercara
Vercara provides a turnkey, multilayered approach to security with UltraDNS, UltraDDoS, and UltraWAF, standalone or bundled as UltraSecure. With Vercara’s comprehensive suite of solutions, organizations gain advanced security capabilities, insights for informed decision-making, and improved resilience against cyber threats.
To learn how Vercara’s suite of solutions can help defend your organization, contact our sales team.
