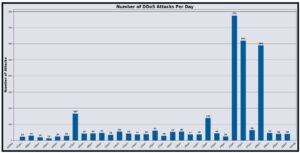
December 2025 reflected a marked escalation in DDoS pressure against DigiCert protected services, with activity increasing in both frequency and persistence relative to the prior month. The month’s activity profile indicates that disruptive attempts were not confined to isolated spikes, but instead sustained at a cadence that increased operational demand. While a large portion of events remained lower in intensity on a per attack basis, the overall pattern points to a more persistent threat environment in which malicious actors relied on repetition and sustained probing to maintain pressure on service availability.
High intensity capability was also more visible throughout December. The month included 23 mega attacks, defined as 100+ Gbps, and the largest observed event reached 1.25 Tbps, classified as a Tsunami DDoS attack. Packet rate extremes were similarly notable, with peak activity reaching 425.61 Mpps and the average packet rate rising to 2,216.18 Kpps. Collectively, these indicators demonstrate that malicious actors retained access to infrastructure capable of delivering both bandwidth saturation and device stressing packet floods, and that December’s activity blended frequent low-cost events with intermittent, high impact bursts intended to stress capacity and defensive operations.
Operational patterns were defined by discrete surge windows rather than evenly distributed background noise. Several days sharply exceeded the monthly daily average and were highly concentrated against individual targets in high value industries, indicating deliberate, campaign style targeting and repeated pressure across multiple periods. Industry targeting was led by IT and Technical Services, followed by Communication Service Providers and Financial Services, consistent with an adversary preference for services where disruption can create downstream impact and operational leverage.
A notable shift in December was the increased presence of carpet bomb style activity. This tactic distributes attack traffic across many IPs within targeted network ranges over short intervals, reducing the effectiveness of simple per destination thresholds and forcing broader mitigation actions that can increase operational friction. The increase suggests malicious actors were optimizing for dispersion and evasion, using breadth to complicate detection, accelerate escalation decisions, and pressure onboarding or mitigation capacity during surge windows. The leading vectors, Total Traffic, UDP, and IP fragmentation, reinforce an emphasis on throughput driven disruption supported by methods that increase defensive workload. Despite the higher tempo, longer durations, and the presence of mega and Tsunami scale events, DigiCert successfully mitigated all observed DDoS activity, maintaining full availability without customer facing service degradation.[JR1]
Stats at a Glance
- Total Number of Attacks: 2,200 (a 106.19% increase compared to November 2025)
- Total number of hours of downtime avoided: ~ 2,100.68 (a 258.91% increase compared to November 2025)
- Number of Mega Attacks (100+ Gbps): 23 (a 155.56% increase compared to November 2025)
- Largest DDoS Attack (Gbps): 2.02
Tbps (a 184.68% increase compared to
November 2025) - Largest DDoS Attack (million packets-per-second): 425.61 Mpps (a 236.34% increase compared to November 2025)
- Longest DDoS Attack: 8.10 Days (a 237.61% increase compared to November 2025)
- Average DDoS Attack (Gbps): 4.31
Gbps - Median DDoS Attacks (Gbps): 0.08Gbps
- Average DDoS Attack (packets-per-second): 2,216.18 Kpps (a 141.59% increase compared to November 2025)
- Median DDoS Attack (packets –per second): 31.34 Kpps
- Average Duration: 57.29 Minutes (a 74.08% increase compared to November 2025)
- Median Duration: 7.75 Minutes (a 5.44% increase compared to November 2025)
- Unique vs Carpet Bombing: 87.91% Unique / 12.09 Carpet Bombing
- Top Three Industry Targeted: IT/Technical Services (79.01%), Communication Services Providers (7.75%), Financial Services (6.85%)