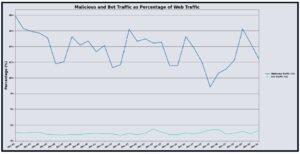
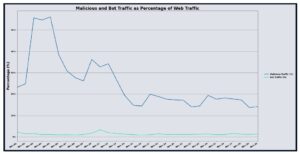
Overall UltraWAF activity in August 2025 showed notable shifts in traffic patterns compared to July. While total web requests decreased slightly by 2.12%, malicious traffic surged significantly, accounting for 62.23% of all observed traffic — an 18.77% increase from the previous month. Bot-related activity also grew modestly, representing 2.69% of overall traffic, up 1.45% from July. These shifts indicate that malicious actors have become increasingly active, leveraging more aggressive exploitation attempts despite a slight decline in overall request volume. The continued rise in malicious traffic highlights a sustained effort by malicious actors to identify vulnerabilities and compromise protected applications.
From an attack vector perspective, Invalid RFC violations remained the most dominant category, representing 58.06% of all malicious traffic. These violations often involve improperly formatted HTTP requests and are commonly linked to automated reconnaissance and scanning activity. The Cookie threat category ranked second with 18.03% of detected attacks, showing persistent attempts to exploit cookie-handling mechanisms for session hijacking and privilege escalation. Command Injection was the third most prevalent category, contributing 6.36%, reflecting ongoing efforts to execute system-level commands through insecure input handling. Additionally, the XML_WSI_ERR_BODY_ENV_NAMESPACE category experienced a 152.37% increase, signaling a surge in SOAP-based exploitation attempts. These attempts target XML Web Services by sending malformed or non-standard SOAP messages to bypass security checks and manipulate backend services.