The US attacks on Iran’s nuclear facilities has elevated an already tenuous international political climate significantly increasing the risk of retaliatory attacks including increased cyber activity. State sponsored and hacktivist activities typically increase when situations like this occur. Any business that is associated with or adjacent to the areas of tension could be impacted at any time so vigilance should be increased across the board. As a DDoS service provider, we always maintain a high level of vigilance because attacks happen all the time across different parts of the market.
Real-Time Intelligence and Vigilance Matter
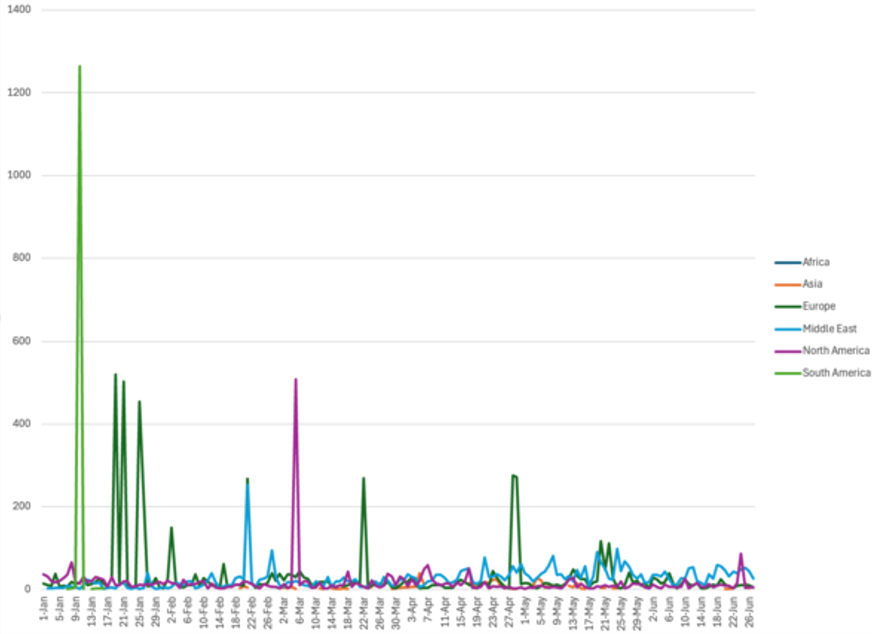
As a matter of course, we track DDoS attacks and application infiltration attempts that we see on our network towards our customers, and we monitor activity within the larger DDoS landscape. DigiCert’s cyber threat intelligence (CTI) team combs through DDoS and WAF exhaust to gauge shifts in quantity of attacks, size, targets, vectors, geographies, industries and many other characteristics to provide customers with visibility and gain some predictability around the threat landscape. When major global events take place, we actively look for signs that specific industries or geographies are being targeted so that we can work proactively with customers that operate in these affected areas. As of this writing, we have seen a slight increase in the volume of attacks towards our customers within the Middle East and to the US but not anything statistically significant. That said, an article by cyber threat organization, Cyble, sites an increase in hacktivism is already taking place.
As a result of the heightened tension, several customers approached us to make sure that we were well prepared to defend them should they get attacked. We explained our approach and the level of diligence that we apply towards detecting threats in real time with automated triggering of mitigations. We took the opportunity to review each customer’s configurations with them to ensure that all their resources were being accounted for, their detection and mitigation settings were optimal, and our lines of communication and runbook were aligned. We’ll also plan to reach out proactively to our customer base should we get any indication that a particular geography or vertical is being targeted.
It is extremely helpful when customers check in proactively like this because it gives us the opportunity to collaboratively review their environment to ensure that we have the best possible protection in place. The adage “you can’t protect what you don’t know about” very much applies to DDoS so it is important to periodically meet with customers to understand their changing environment, the IP address space they cover, what applications they run, typical traffic patterns, and any critical events that are taking place. Relying solely on technology to “learn” the network tends to produce a lot more false positives and unintended consequences. It’s also best practice to ensure that all contact information for the customer is up to date and the customer has the correct contact information for our service. These review sessions will produce a much tighter defense.
DDoS Review Checklist
DDoS service reviews don’t have to wait until there is an imminent threat of attack. The best time to do them is during times of relative quiet where resources aren’t spread thinly. The best practice for DDoS defense is to conduct a service review at a minimum annually.
The following is a checklist of areas that a comprehensive service review could cover:
- Validation of IP subnets and applications being protected.
- Review of any new applications/services that have been launched and any upcoming events that may impact applications/services.
- Audit of historical alerts and fine tuning of detection settings for applications and network segments.
- Review and tuning of default DDoS protection measures per application or network segment.
- If applicable, creation of custom detection and mitigation measures for strategic and/or unique applications such as VPN, proxies, SD-WAN, DNS, and VOIP.
- Ensure the customer has all the correct contact information for the service including phone numbers and web portal addresses.
- Review of customer runbook to make sure it reflects the correct operational flows.
- Verify customer contact information is up to date.
- If the customer is on-demand, a re-direction test to ensure path integrity.
- Periodically, customers can choose to hire a DDoS testing company to test out their DDoS defenses.
Access to good cyber threat intelligence is an important factor in DDoS defense as it can inform you when you are under high or imminent risk. These times of crisis often drive businesses to take action to ensure their defenses are solid and we are here to help provide that assurance and make any adjustments necessary. However, there is no reason to wait for a time of crisis to make these checks. In DDoS defense, conducting service reviews regularly is a best practice as it puts organizations in the best possible position to fight off any attack that may come their way.
