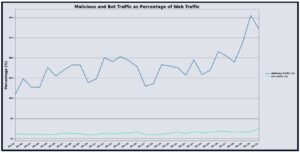
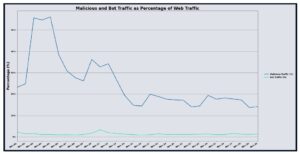
In December 2025, UltraWAF processed approximately 1.87 trillion web requests, a 3.13% increase compared to November 2025. Malicious traffic declined materially, with 14.86% of requests identified as malicious, a 39.90% decrease month over month. Bot traffic represented 1.23% of total requests and decreased by 5.83%. The combined effect was higher overall request volume alongside a substantially lower malicious share, suggesting that the month’s activity was driven more by baseline demand while malicious actors continued probing at lower relative intensity.
The most significant behavioral shift was a 97.71% increase in XML_WSI_ERR_BODY_ENV_NAMESPACE violations. This pattern is consistent with concentrated probing of SOAP and XML web service endpoints using nonstandard or intentionally confusing namespace constructions. Namespace sensitivity is central to SOAP processing, and mismatches can expose differences in how inspection engines and backend services parse the same message. Spikes in this category often align with reconnaissance designed to identify parser edge cases and inconsistent handling paths that can be leveraged to reach downstream XML processing operations. Across broader attack methods, activity remained heavily skewed toward input manipulation, with Cookie-based threats accounting for 45.72% of malicious detections, and continued pressure from Command Injection at 15.73% and Field Format violations at 16.48%, reflecting sustained attempts to exploit weak parsing, validation, and interpreter boundaries.
Observed payloads in December show breadth across web frameworks, CMS platforms, and embedded device interfaces, with repeated attempts to convert routine parameters into execution or disclosure primitives. Multiple payloads targeted file read and file write behaviors, including local file inclusion leading to remote code execution through PEAR utilities, and direct file disclosure attempts against WordPress plugin download handlers and dompdf paths. SQL injection remained present in both UNION-based and time-based forms, indicating efforts to validate database control even when errors or output are suppressed. Several requests reflected exploitation patterns associated with high-impact platform weaknesses, including server-side template or script evaluation (for example, Jelly style evaluation probes), command injection one-line downloaders against LuCI endpoints, and crafted GraphQL queries intended to stress parsers and handlers. Additional activity targeted application logic abuse and enumeration, including XWiki redirect chaining to trigger internal actions, XWiki search queries aimed at harvesting user or configuration artifacts, and direct API enumeration attempts against services such as Nacos using JWT-like tokens.
Overall, December’s activity reflects continued, method-driven probing focused on parsers, interpreters, and exposed administrative or API surfaces, with a notable emphasis on XML and SOAP edge-case testing. The payload set reinforces that malicious actors are simultaneously pursuing quick validation signals, such as deterministic hashes, timing delays, and marker strings, while also attempting framework-specific exploit chains that can enable file disclosure, account creation, or remote execution when a vulnerable component is present. Taken together, the month indicates lower malicious volume relative to total traffic, but persistent breadth in attack techniques and continued experimentation against widely deployed platforms.
Stats at a Glance
- Total Web Requests: 1,877,715,527 (3.13% increase from November 2025)
- Largest Threat Category: Cookie (45.72%)
- Total WAF Violations: 279,069,366
- Top Three Industry Targeted: Travel/Hospitality (71.70%), Financial (24.95%), Technology/Security (1.48%)
- Total Bot Violations: 23,086,696
- Top Three Source Countries: Great Britain (70.56%), United States (12.46%), France (1.06%)