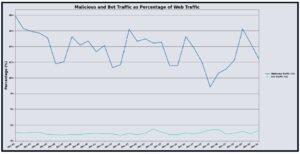
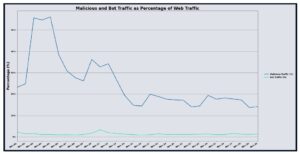
In January 2026, DigiCert’s UltraWAF processed more than 2.17 trillion web requests, a 15.74% increase compared to December 2025. Malicious traffic grew faster than overall volume, with approximately 18.21% of requests, more than 395 million, identified as malicious, representing a 41.80% month over month increase. Bot traffic also rose to roughly 1.41% of total requests, more than 30 million, up 32.54% from the prior month. Together, these shifts indicate a clear increase in automated and hostile interaction with protected applications, elevating operational risk and reinforcing the need for sustained hardening and monitoring.
Detection patterns remained concentrated, with Cookie related detections representing 49.28% of malicious traffic, followed by Command Injection at 16.34% and Field Format at 14.37%. The most notable change within this profile was a sharp rise in Buffer Overflow Cookie events, increasing 176.16% from December. This category is significant because it aligns less with routine web injection activity and more with traffic characteristics consistent with memory corruption probing. In practice, this can reflect attempts to trigger buffer overflow conditions in components that handle untrusted input, and it is often associated with automated exploitation tooling seeking remote code execution. The broader category mix suggests malicious actors prioritized high throughput automation that abuses session or state handling, attempts to coerce applications into executing operating system commands, or forces malformed and unexpected parameter structures to stress validation logic.
Observed payloads reinforce that the dominant intent was server-side execution followed by rapid second stage delivery. UltraWAF detected PHP runtime directive manipulation designed to enable allow_url_include and prepend php://input, which can enable attacker supplied code execution in susceptible PHP CGI configurations. Additional payloads targeted common framework exploitation patterns, including ThinkPHP invocation via call_user_func_array with system() to run shell commands, and XWiki macro injection using {{groovy}} to execute sh -c and launch a downloader chain. These payloads repeatedly leveraged fallbacks across wget, busybox wget, and curl to retrieve remote scripts, reflecting standardized automation designed to execute reliably across diverse Linux environments. Other payloads show continued probing for exposed administrative and debugging surfaces. Requests to /_ignition/execute-solution align with attempts to abuse Laravel Ignition debug functionality when exposed. A Log4j style JNDI LDAP payload used obfuscation to assemble a lookup and included a Base64 decoded command chain intended to fetch and execute a miner related script (4thepool_miner.sh). Reconnaissance against the JBoss jmx-console/HtmlAdaptor endpoint further indicates systematic discovery of exposed management interfaces used to gather version and environment details for follow on exploitation.
In summary, January reflected increased exploitation-oriented pressure, emphasizing code execution attempts, staged downloader behavior, and reconnaissance for exposed debug or management interfaces. Continued focus on patch cadence, strict access control for administrative endpoints, and monitoring for exploit precursors such as repeated overflow style probing, command execution attempts, and suspicious outbound retrieval patterns remains critical to reducing risk and limiting impact.
Stats at a Glance
- Total Web Requests: 2,173,288,518 (a 15.74% increase from December 2025)
- Largest Threat Category: Cookie (49.28%)
- Total WAF Violations: 395,714,280 (a 14.80% increase from December 2025)
- Top Three Industry Targeted: Travel/Hospitality (76.29%), Financial (18.93%), Government (3.42%)
- Total Bot Violations: 30,598,590 (a 32.54% increase from December 2025)
- Top Three Source Countries: Great Britain (74.68%), United States (12.35%), Netherlands (0.96%)